D3FENDOT
Background
D3FEND was designed to model computers, devices, computer networks, and their associated information flows. After our initial release, we received frequent requests for the ability to apply the ontology to specific domains, including cyber-physical systems. These systems are programmed to sense and effect physical changes in their environments through sensors and actuators respectively. Systems whose control processes sense and produce physical effects are known as Operational Technology (OT) and have their own distinct cybersecurity properties; thus: we introduce D3FEND for OT. We take a broad view of OT and intend to extend this work to additional domains—for example, space.
Purpose and Scope
Our primary goal in D3FEND for OT is to enable application of the D3FEND Ontology to OT environments. Because information technology (IT) and OT share a common foundation, D3FEND’s unified technology ontology accommodates additions for OT-specific concepts; these additions extend the core ontology rather than forming a separate body of work.
D3FEND for OT enables OT engineers, security engineers, and cyber threat intelligence analysts to model their security scenarios using the D3FEND ontology. New OT specific artifacts such as controllers, sensors, actuators, OT events, countermeasures, and OT network components are mapped to linked to other OT resources where possible.
What it is:- An extension of the D3FEND ontology tailored to operational technology domains, adding OT-specific artifacts, events, and countermeasures.
- A high-fidelity modeling framework for OT engineers, defenders, and cyber threat intelligence analysts to represent systems, threats, and detections in CAD or SysML (please contact us to use D3FEND in SysML).
- A bridge to existing OT resources, including mappings to ATT&CK for ICS and relationships among artifacts and techniques.
- A separate or standalone ontology or framework that replaces core D3FEND—it builds on and extends the core.
- A comprehensive or complete model of the OT domain.
- A compliance checklist, product catalog, or prescriptive configuration guide.
- A replacement for existing OT cybersecurity standards or guidance.
Quick Start
Applying D3FEND for OT to your scenario requires foundational knowledge that is outside the scope of this page, which focuses on the added OT content. Please see our quick start blog post, "Getting Started with D3FEND for OT", which walks through the basics.
Intended Audience & Use Cases
D3FEND for OT was developed for the following roles and use cases.
| Role | Use Case |
|---|---|
| OT Defensive Cyber Engineer |
|
| OT Cyber Threat Intel Analyst |
|
| OT Systems Architect |
|
| OT Systems Acquisition Specialist |
|
Example OT-focused D3FEND Graphs

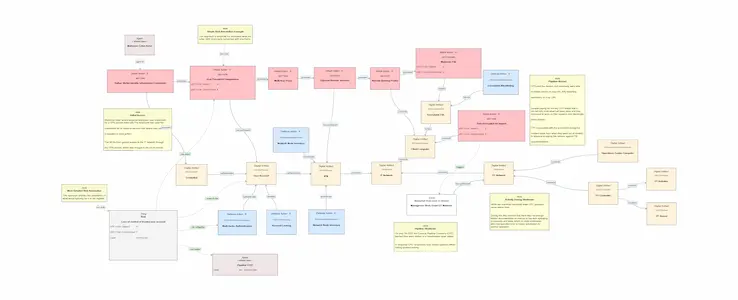
NotPetya Ransomware Attack
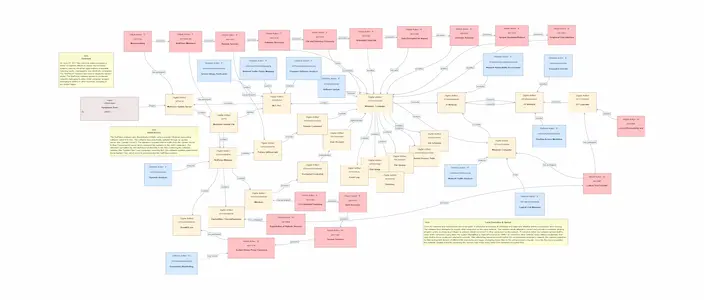
Water System Unitronics PLC Attacks
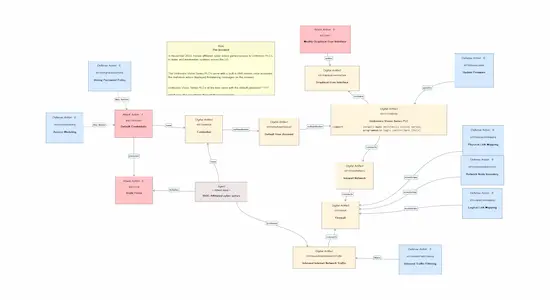
TRITON
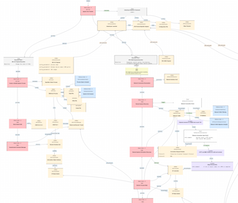
Industroyer Attack
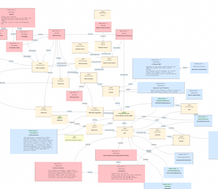
Black Energy
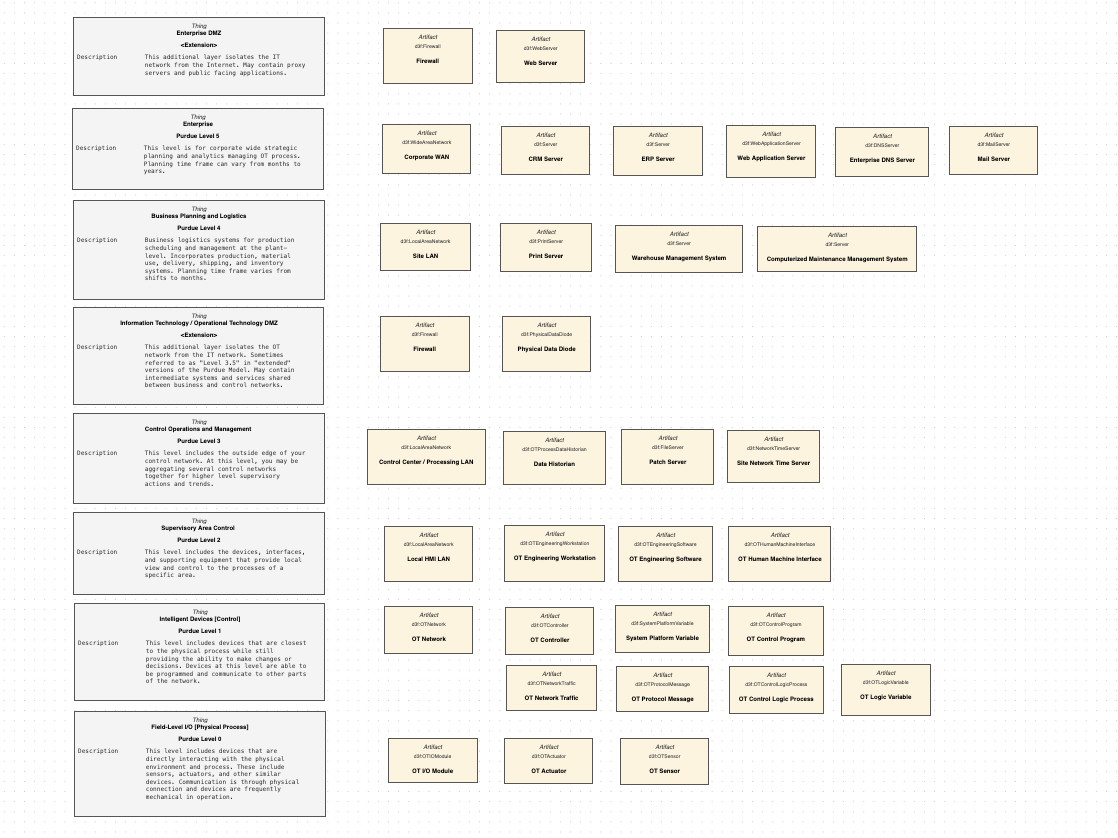
Detailed Purdue Model Represented in the D3FEND Ontology
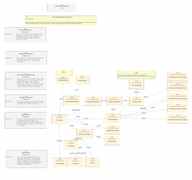
Simple Purdue Model Represented in the D3FEND Ontology
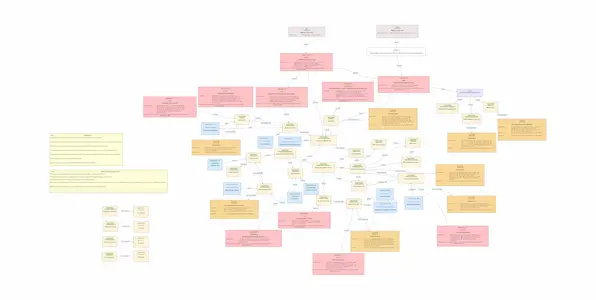
Electric Vehicle Regenerative Braking System
Ontology Additions
ATT&CK ® for ICS
MITRE ATT&CK for ICS has also been added to the D3FEND Ontology for use in CAD as a part of D3FEND for OT.
OT Countermeasures
The following are the new defensive techniques added to the D3FEND ontology. Not included below are the additional new relationships between existing countermeasures to the new OT Artifacts which have also been added.
| Name | Defensive Property | Range | Description |
|---|---|---|---|
| Change Default Password | strengthens, hardens | Password, User Account,OT Controller | Changing the default password means replacing the factory-set credentials with a strong, unique password before the device is deployed, preventing unauthorized access. |
| Domain Logic Validation | validates | Subroutine | Validation of variable state in the context of the domain application. |
| Operational Logic Validation | validates | OT Control Function | Validation of variable state in the context of the control logic of the operational application. |
| Remote Firmware Update Monitoring | monitors, detects | OT Network Traffic, OT Device Firmware Command | Monitoring of remote firmware update commands to identify unauthorized software installations. |
| Platform Uptime Monitoring | monitors | Platform Uptime | Monitor the amount of time since the last power cycle or restart. |
| Operational Process Monitoring | uses | OT Process Data Historian | Monitoring physical parameters and operator actions related to an operational environment. |
| Operating Mode Monitoring | monitors | Operating Mode | Detects operating modes such as Program, Run, Remote, or Stop. |
| Operating Mode Restriction | restricts | Operating Mode | Restricting unauthorized changes to the operating mode prevents devices from switching into inappropriate or vulnerable states during normal use. |
| Physical Access Mediation | isolates | Physical Artifact | Physical access mediation is the process of granting or denying specific requests to enter specific physical facilities (e.g., Federal buildings, military establishments, border crossing entrances.) |
| Physical Locking | mediates-access-to | Computer Enclosure | Employ a mechanical locking device for securing moveable portions of physical barriers (e.g., doors, gates, drawers) in a secured position. |
| OT Variable Access Restriction | limits, restricts | OT Logic Variable, OT Write Command | Assign read/write access controls on designated registers or data tags to prevent unauthorized writes. |
| User Group Permissions | restricts | User Group | Access control where access is determined based on attributes associated with users and the objects being accessed. |
| Directional Network Link | restricts | Physical Link | Enforce one-way network communication by preventing two-way communication. |
| Hardware-based Write Protection | hardens | Storage | Physical methods of preventing data from being written to computer storage. |
| Physical Enclosure Hardening | hardens | Computer Enclosure | Physical changes to a computer enclosure which reduce the ability for agents or the environment to affect the contained computer system. |
| Application Performance Monitoring | monitors | Log, System Application Cycle Count, Application Failure Count Variable, Application Scan Time | Monitoring the count and duration of the application or program cycle. |
| Application Exception Monitoring | monitors | Log, Application Failure Count Variable | Monitoring the failures of system counters and timers. |
Key Digital Artifacts and Events
The following are the artifacts and events added to the D3FEND ontology as a part of the D3FEND for OT effort.
| Name | Description |
|---|---|
| Computer Cabinet | A computer cabinet houses one or more computers and can range in size and material. |
| Computer Case | A computer case is a computer enclosure which encloses a single primary computer. |
| Computer Enclosure | A part providing protection of computer equipment against certain external influences and protects against direct contact. |
| Data Acquisition Agent | A software component which connects to data sources to gather raw, time-stamped data. It often connects to databases or historian gateways for storage and analysis. |
| Data Acquisition Unit | The hardware component which connects to data sources to gather raw, time-stamped data. It often connects to databases or historian gateways for storage and analysis. |
| Digital Access Badge | A credential used to gain entry to an area having automated access control entry points. Example media being magnetic stripe, proximity, barcode, or smart cards are examples. |
| Digital Camera | An optical instrument that can capture an image. A digital camera that captures photographs in digital memory. |
| Electronic Combination Lock | A system comprised of an automatic door closer on the door, an input device, a controlling device, and a lock, usually mechanical, which is released or activated when the correct combination is entered or correct token is presented. |
| HMI Application | Application software which runs the main program in an HMI. |
| HMI Application Process | The instructions within an HMI defined by user programming to interpret visual (and potentially audio) inputs and define visual (and potentially) audio outputs. |
| Motion Detector | An electrical device that utilizes a sensor to detect nearby motion. |
| Operating Mode | The Operating Mode designates the specific, selectable state of an OT controller that delineates its operational behavior and governs access to engineering functions, commonly including Program, Run, Remote, Test, or Stop. |
| OT Actuator | An OT actuator is an industrial-grade actuator optimized for operational technology (OT) environments, such as SCADA or process-control systems. It tolerates harsher conditions, meets stricter safety and reliability standards, and integrates seamlessly with ICS protocols to enable real-time mechanical motion or adjustments in production lines and critical infrastructure. |
| OT Controller | An OT Controller is an industrial control device that automatically regulates one or more controlled variables in response to command inputs and real-time feedback signals. |
| OT Control Logic Process | The instructions and algorithms within an OT Controller defined by user programming to interpret inputs, process information, and determine outputs. |
| OT Control Program | The file stored in controller memory that is used to operate the controller. |
| OT Embedded Computer | A ruggedized computational device, embedded in industrial control systems, designed to handle real-time tasks and environmental stressors common in OT. |
| OT Engineering Software | Software used in an industrial process to help engineers design, test, and maintain OT. This software enables the programming of OT controllers. |
| OT Engineering Workstation | An Engineering Workstation (EWS) is used to perform various maintenance, configuration, or diagnostics functions for a control system. The EWS will likely require dedicated application software to interface with various devices (e.g., RTUs, PLCs), and may be used to transfer data or files between the control system devices and other networks. |
| OT Event (45 subclasses) | A discrete occurrence within an operational technology environment that denotes a significant change in state, execution of a command, or transmission of information. |
| OT Human Machine Interface | Human-Machine Interfaces (HMIs) are systems used by an operator to monitor the real-time status of an operational process and to perform necessary control functions, including the adjustment of device parameters. |
| OT I/O Module | An I/O Module is a hardware device that translates signals between external sensors or actuators and control systems. It typically handles analog-to-digital (and vice versa) conversion, serving as the data interface that allows physical processes to be monitored and controlled by digital controllers. |
| OT Mode Switch | An OT Mode Switch is a dedicated mechanism, implemented as either a physical keyswitch or a software control, that permits authorized users to transition an OT controller between its operating modes. |
| OT Network | A computer network which connects OT devices. |
| OT Network Traffic | Network traffic generated by operational technology devices, e.g. programmable logic controllers |
| OT Power Supply | An OT power supply is a power supply whose control amplifier is optimized for signal-processing tasks rather than supplying mere steady-state power to a load. It is a self-contained combination of operational amplifiers, power amplifiers, and integral power circuits designed for higher-level operations in industrial or OT contexts. |
| OT Process Data Historian | A system used to collect and store data, including telemetry, events, alerts, and alarms about the operational process and supporting devices. |
| OT Protocol Message (45 subclasses) | Packets generated by an operational technology protocol contain an OT protocol message. |
| OT Sensor | An OT Sensor is an industrial-grade sensing device engineered for operational technology (OT) environments (e.g. SCADA, ICS). It measures physical variables—such as pressure, temperature, or flow—under demanding conditions, converting them into reliable signals for real-time monitoring and process control loops. |
| Physical Access Alarm Event (3 subclasses) | An event occurring when combination lock's bolt changes position. |
| Physical Data Diode | A device that physically enforces one-way (unidirectional) network communication. |
| Physical Key | A physical key is used to operate a lock, typically metal, designed with specific markers that match the internal mechanism of a lock, allowing it to rotate the lock when inserted. |
| Physical Key Lock | A mechanical locking device for securing moveable portions of physical barriers (e.g., doors, gates, drawers) in a secured position. |
| Proximity Sensor | A sensor able to detect the presence of nearby objects without any physical contact. |
| Runtime Variable (11 subclasses) | A runtime variable is an abstract storage location paired with an associated symbolic name, which contains some known or unknown quantity of data or object referred to as a value, which can change during the execution of a computer program. |
| Time Series Database | A specialized database optimized for storing and retrieving time-stamped data. |
| Write Protect Switch | A physical device used to restrict configuration of a device. |
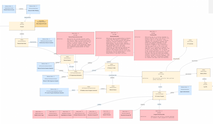
OT Weaknesses and Vulnerabilities - CWE & CVE
Based on public reporting, we have identified CVEs and CWEs relevant to OT device manufacturers. We have modeled them against the new D3FEND for OT ontology additions in order to illustrate which parts of the devices were affected, and how they related to the D3FEND Ontology.Open in D3FEND CAD